Understanding data protection harms
What consequences are we trying to prevent?
We hear a lot about data protection risks, but equally important is knowing what data protection harms look like. Harms are essentially the range of potential consequences for individuals, or indeed society more broadly, should data protection risks materialise.
Insufficient training, weak access controls, ‘invisible’ processing and over-retention of personal data are just some examples of data protection risks which, if left unaddressed or if an incident occurs, could cause harm to individuals.
When conducting risk assessments (such as Legitimate Interests Assessments, DPIAs and AI Assessments) we don’t just need to identify the risks, we also need to think about what possible outcomes and harms we are trying to prevent. And crucially when a data breach occurs, we need to know the consequences this could have for those affected – the harm it could cause.
In our experience, assessments and data breach plans don’t always clearly spell out the nature of harm which could materialise if the appropriate measures and controls are not put in place to prevent or mitigate them.
This is where the ICO’s Taxonomy of Data Protection Harms is a useful document. It includes a non-exhaustive table of harms, which would be a handy appendix to any DPIA template or Data Incident Procedure.
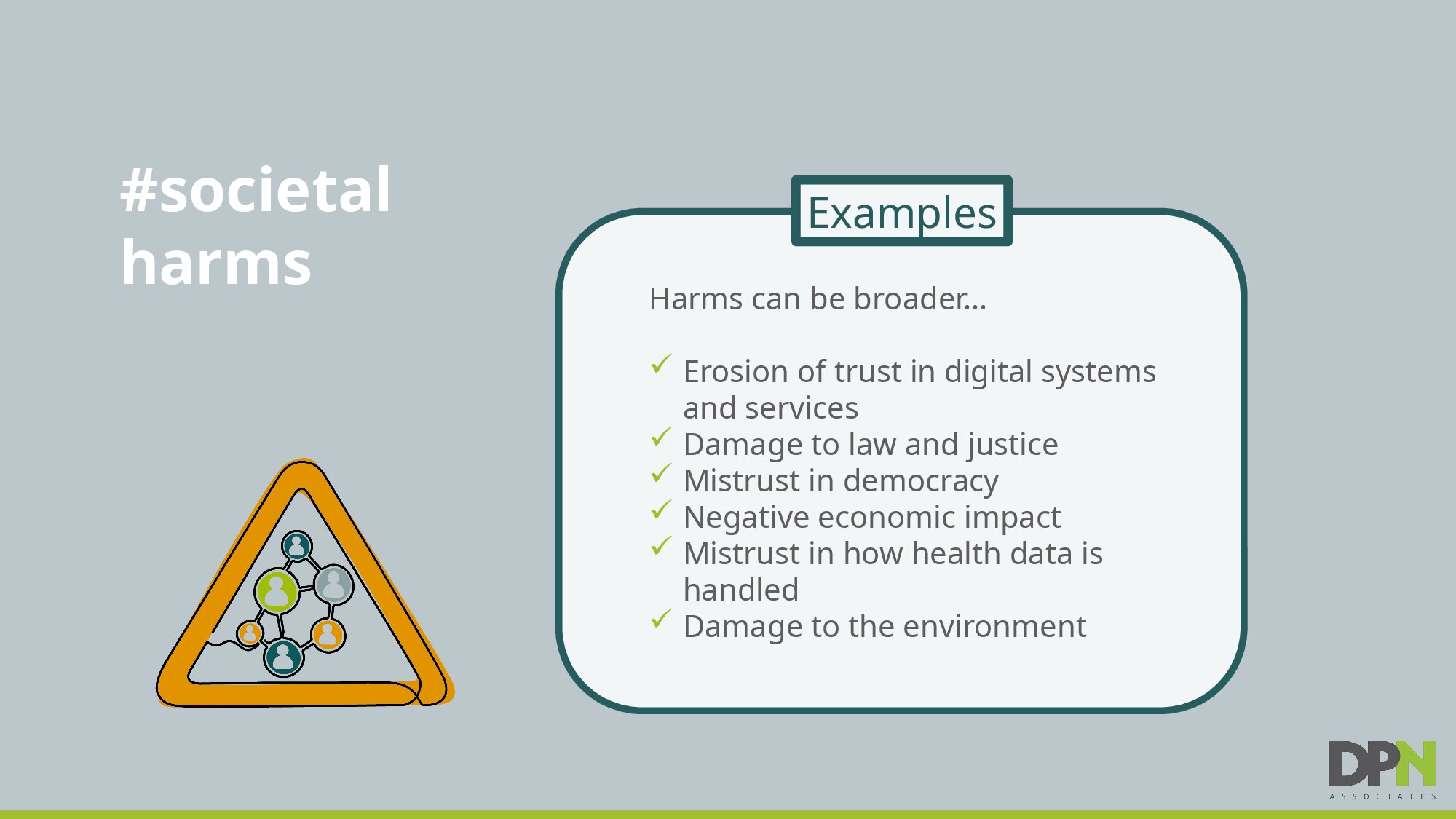
Data protection harms aren’t always obvious. They can be nuanced, complex, overlapping or more intangible. Financial loss may be easier to gauge than psychological damage. We need to assess both the likelihood of harm and its severity.
Broadly using the ICO’s taxonomy here are some examples of data protection harms: